| Password Audits – Focus on the Admins | 2019-05-09 17:30 |
Have you considered adding periodic password audits to your corporate security plan? Compared to the cost of a security breach or standard pentest, periodic password audits are relatively inexpensive (e.g., on the order of $7K/quarter for a single medium-sized domain), yet they shed light on an important aspect of security that management has little ability to control: the passwords that administrators and end users choose.
In this article, I discuss the impact of weekly audits on chosen admin passwords over a 4-year period.
In Cracking Grid – Essential Attributes, I asserted that "it shouldn't take much to convince you that user credentials (and password hashes by extension) are highly sought after items". While any given username/password pair can present a toehold opportunity (e.g., a machine here, a few resources there, etc.), an administrative-level username/password pair often presents a complete and unparalleled takeover opportunity. As a security professional, it should be one of your worst nightmares.
But what can you do about it? You've defined a corporate password policy; you've stressed the importance of creating complex passwords; and yet, you have no idea where you really stand when it comes to password security.
One answer is periodic password audits ... Why? Below are a number of reasons you should consider.
- They give you a sense of how resistant company passwords are to focused, time-limited attacks.
- They can reveal policy gaps/violations (e.g., short passwords, not enough character diversity, etc.).
- They can reveal behavioral patterns that would otherwise go unnoticed (e.g., use of company name or other corporate culture isms during password creation).
- They can reveal procedural patterns that degrade security (e.g., helpdesk setting pattern-based, weak, default, or even empty passwords).
- They can reveal accounts that share a common password (e.g., system/service accounts, accounts whose passwords were reset, unused/dormant accounts, etc.).
- They can aid in detecting users circumventing password reuse restrictions (e.g., across domains, between admin/non-admin accounts used by the same individual, history violations, etc.).
- They allow you prove that a user's password is weak/guessable even when that user insists his/her password is "strong".
- They allow you to collect metrics, measure progress, and determine if you are trending in the right direction(s).
- They allow you develop a more effective training program (e.g., by identifying those who need the most attention, making it possible to target the most common mistakes, increasing data breach awareness, etc.).
The graph below quite aptly shows the impact of weekly audits on chosen admin passwords over a 4-year period for a single corporate domain (code name "ACME"), and since our client elected to conduct weekly audits, the resolution achieved in the dataset is exceptional. For example, it's evident that the password recovery rate is in an overall downtrend (from approximately 75% to single digits). Additionally, it's clear that the trend is not linear. Note how the recovery rate dropped sharply from from 75% to 50% in first weeks of 2015, but it took almost 2 years to fall below 25%, and another 2 years to approach zero. The ride down was bumpy as well (i.e., there are visible ups and downs from week to week as admins sought to create passwords that would withstand our attacks and we sought to improve the effectiveness of our cracking grid).
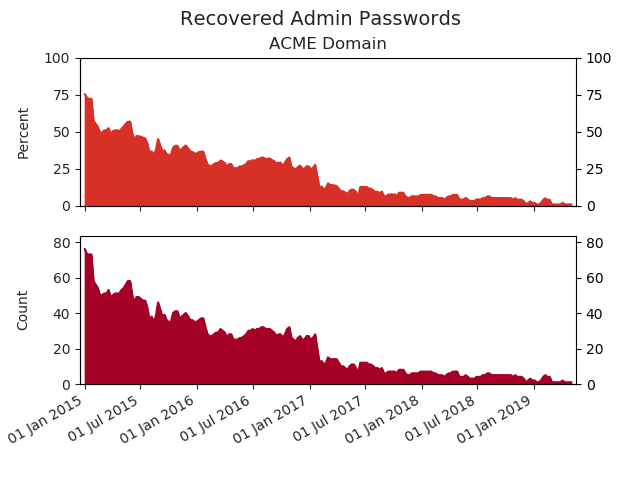
Is a picture worth a thousand words? Maybe. Maybe not. But in this particular case, it's worth knowing that 75+ admins have passwords strong enough to withstand KoreLogic's weekly pounding, and that should help take the edge off that nightmare you've been having.
| Posted by Klayton at: 17:30 permalink |
